CCNA1 Final Exam & Answer

Soal Beserta jawaban Latihan CCNA 1
Final Exam
STMIK Nusa Mandiri Jakarta
1. Which two commands can be used on a Windows host to display the
routing table? (Choose two.)
tracert
route
print
show
ip route
netstat
-s
netstat
-r
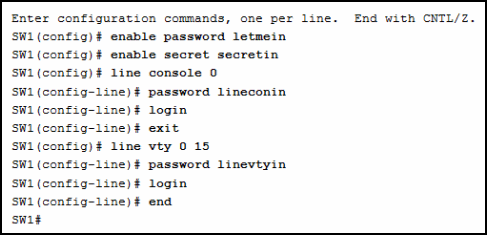
SW1# configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
<output omitted>
SW1(config)# enable password letmein
SW1(config)# enable secret secretin
SW1(config)# line console 0
SW1(config-line)# password lineconin
SW1(config-line)# login
SW1(config-line)# exit
SW1(config)# line vty 0 15
SW1(config-line)# password linevtyin
SW1(config-line)# end
SW1#
Enter configuration commands, one per line. End with CNTL/Z.
<output omitted>
SW1(config)# enable password letmein
SW1(config)# enable secret secretin
SW1(config)# line console 0
SW1(config-line)# password lineconin
SW1(config-line)# login
SW1(config-line)# exit
SW1(config)# line vty 0 15
SW1(config-line)# password linevtyin
SW1(config-line)# end
SW1#
Refer to the exhibit. A network administrator is configuring
access control to switch SW1. If the administrator has already logged into a
Telnet session on the switch, which password is needed to access privileged
EXEC mode?
letmein
secretin
lineconin
linevtyin
3. After making configuration changes on a Cisco switch, a network administrator issues a copy running-config startup-config command. What is the result of issuing this command?
The
new configuration will be stored in flash memory.
The
new configuration will be loaded if the switch is restarted.
The
current IOS file will be replaced with the newly configured file.
The
configuration changes will be removed and the original configuration will be
restored.
4. Which subnet would include the address 192.168.1.96 as a usable host address?
192.168.1.64/26
192.168.1.32/27
192.168.1.32/28
192.168.1.64/29
5. Which procedure is used to reduce the effect of crosstalk in copper cables?
designing
a cable infrastructure to avoid crosstalk interference
wrapping
the bundle of wires with metallic shielding
avoiding
sharp bends during installation
requiring
proper grounding connections
twisting
opposing circuit wire pairs together
6. What is an example of a top-level domain?
cisco.com
www.cisco.com
.com
root.cisco.com
7. During the encapsulation process, what occurs at the data link layer for a PC connected to an Ethernet network?
The
process port number is added.
The
logical address is added.
An
IP address is added.
The
physical address is added.8. What are two characteristics shared by TCP and UDP? (Choose two.)
use
of checksum
port
numbering
connectionless
communication
3-way
handshake
default
window size
ability
to to carry digitized voice
9. A network administrator is troubleshooting connectivity issues on a server. Using a tester, the administrator notices that the signals generated by the server NIC are distorted and not usable. In which layer of the OSI model is the error categorized?
network
layer
data
link layer
physical
layer
presentation
layer
10. A network engineer is analyzing reports from a recently
performed network baseline. Which situation would depict a possible latency
issue?
a
next-hop timeout from a traceroute
an
increase in host-to-host ping response times
a
change in the amount of RAM according to the show version output
a
change in the bandwidth according to the show interfaces output
11. What layer is responsible for routing messages through an internetwork in the TCP/IP model?
network
access
internet
transport
session
12. Which command can an administrator issue on a Cisco router to send debug messages to the vty lines?
terminal
monitor
logging
synchronous
logging
console
logging
buffered
13. What is one indication that a Windows computer did not receive an IPv4 address from a DHCP server?
The
computer cannot ping 127.0.0.1.
The
computer cannot ping other devices on the same network with IP addresses in the
169.254.0.0/16 range.
Windows
displays a DHCP timeout message.
The
computer receives an IP address that starts with 169.254.14. How many usable IP addresses are available on the 192.168.1.0/27 network?
256
254
62
16
32
30
16. What subnet mask is needed if an IPv4 network has 40 devices
that need IP addresses and address space is not to be wasted?
255.255.255.224
255.255.255.128
255.255.255.0
255.255.255.240
255.255.255.192
17. Which switching method has the lowest level of latency?
cut-through
fast-forward
store-and-forward
fragment-free
18. Why are port numbers included in the TCP header of a segment?
to
enable a receiving host to forward the data to the appropriate application
to
determine which Layer 3 protocol should be used to encapsulate the data
to
indicate the correct router interface that should be used to forward a segment
to
identify which switch ports should receive or forward the segment
to
allow the receiving host to assemble the packet in the proper order
19. Which two protocols operate at the highest layer of the TCP/IP
protocol stack? (Choose two.)
IP
POP
TCP
Ethernet
DNS
UDP
20. Under which two circumstances will a switch flood a frame out of
every port except the port that the frame was received on? (Choose two.)
The
source address in the frame header is the broadcast address.
The
destination address is unknown to the switch.
The
source address in the frame is a multicast address.
The
frame has the broadcast address as the destination address.
The
destination address in the frame is a known unicast address.
21. What function does pressing the Tab key have when entering a
command in IOS?
It
exits configuration mode and returns to user EXEC mode.
It
moves the cursor to the beginning of the next line.
It
completes the remainder of a partially typed word in a command.
It
aborts the current command and returns to configuration mode.
22. A network administrator is measuring the transfer
of bits across the company backbone for a mission critical financial
application. The administrator notices that the network throughput appears
lower than the bandwidth expected. Which three factors could influence the
differences in throughput? (Choose three.)
the
amount of traffic that is currently crossing the network
the
sophistication of the encapsulation method applied to the data
the
type of traffic that is crossing the network
the
latency that is created by the number of network devices that the data is
crossing
the
bandwidth of the WAN connection to the Internet
the
reliability of the gigabit Ethernet infrastructure of the backbone
23. What are the three ranges of IP addresses that are reserved for
internal private use? (Choose three.)
192.168.0.0/16
192.31.7.0/24
64.100.0.0/14
127.16.0.0/12
10.0.0.0/8
172.16.0.0/12
24. What protocol is responsible for controlling the size of
segments and the rate at which segments are exchanged between a web client and
a web server?
TCP
Ethernet
IP
HTTP
25. A network technician is attempting to configure an interface by
entering the following command: SanJose(config)# ip address 192.168.2.1
255.255.255.0. The command is rejected by the device. What is the reason
for this?
The
subnet mask information is incorrect.
The
command is being entered from the wrong mode of operation.
The
command syntax is wrong.
The
interface is shutdown and must be enabled before the switch will accept the IP
address.
26. What is a characteristic of multicast messages?
They
are sent to all hosts on a network.
They
are sent to a select group of hosts.
They
must be acknowledged.
They
are sent to a single destination.
29. How does quality of service help a network support a wide range
of applications and services?
by
providing mechanisms to manage congested network traffic
by
allowing quick recovery from network failures
by
providing the ability for the network to grow to accommodate new users
by
limiting the impact of a network failure
30. Which firewall feature is used to ensure that packets coming
into a network are legitimate responses to requests initiated from internal
hosts?
URL
filtering
packet
filtering
application
filtering
stateful
packet inspection
33. Which statement is true about variable-length subnet masking?
Each
subnet is the same size.
The
size of each subnet may be different, depending on requirements.
Subnets
may only be subnetted one additional time.
Bits
are returned, rather than borrowed, to create additional subnets.
35. What is a characteristic of the LLC sublayer?
It
provides delimitation of data according to the physical signaling requirements
of the medium.
It
provides the logical addressing required that identifies the device.
It
places information in the frame allowing multiple Layer 3 protocols to use the
same network interface and media.
It
defines software processes that provide services to the physical layer.
36. What will a host on an Ethernet network do if it receives a
frame with a destination MAC address that does not match its own MAC address?
It
will remove the frame from the media.
It
will strip off the data-link frame to check the destination IP address.
It
will forward the frame to the next host.
It
will discard the frame.
37. Option 6: the first
entrance into the CLI of an IOS device. Press spacebar to enter matching
mode.
Match the description with the associated IOS mode. (Not all
options are used.)
changes made affect
the operation of the device as a whole
accessed by entering
the enable command
limited number of
basic monitoring commands
accessed by entering
the configure terminal command
the first entrance
into the CLI of an IOS device
used to enable the password for vty lines
user EXEC mode
limited number of basic monitoring commands
the first entrance into the CLI of an IOS device
privileged EXEC mode
accessed by entering the enable command
identified by a prompt ending with the # character
global configuration mode
changes made affect the operation of the device as a whole
accessed by entering
the configure terminal command
38. Which service provides dynamic global IPv6 addressing to end
devices without using a server that keeps a record of available IPv6 addresses?
stateful
DHCPv6
stateless
DHCPv6
SLAAC
static
IPv6 addressing
39. If a device receives an Ethernet frame of 60 bytes, what will it
do?
drop
the frame
process
the frame as it is
add
random data bytes to make it 64 bytes long and then forward it
send
an error message to the sending device
40. What are two ways that TCP uses the sequence numbers in a
segment? (Choose two.)
to
specify the order in which the segments travel from source to destination
to
limit the number of segments that can be sent out of an interface at one time
to
identify missing segments at the destination
to
determine if the packet changed during transit
to
reassemble the segments at the remote location
42. A company is expanding its business to other countries. All
branch offices must remain connected to corporate headquarters at all times.
Which network technology is required to support this requirement?
MAN
LAN
WAN
WLAN
44. What are the three primary functions provided by Layer 2 data
encapsulation? (Choose three.)
detection
of errors through CRC calculations
error
correction through a collision detection method
data
link layer addressing
session
control using port numbers
placement
and removal of frames from the media
conversion
of bits into data signals
delimiting
groups of bits into frames
45. At a minimum, which address is required on IPv6-enabled
interfaces?
link-local
unique
local
global
unicast
site
local
46. What unique address is embedded in an Ethernet NIC and used for
communication on an Ethernet network?
IP
address
host
address
MAC
address
network
address
48. What purpose does NAT64 serve in IPv6?
It
converts IPv6 packets into IPv4 packets.
It
converts regular IPv6 addresses into 64-bit addresses that can be used on the
Internet.
It
enables companies to use IPv6 unique local addresses in the network.
It
converts the 48-bit MAC address into a 64-bit host address that can be used for
automatic host addressing.
It
translates private IPv6 addresses into public IPv6 addresses.
49. What are two characteristics of Ethernet MAC addresses? (Choose
two.)
MAC
addresses must be unique for both Ethernet and serial interfaces on a device.
They
are globally unique.
They
are expressed as 12 hexadecimal digits.
They
are routable on the Internet.
MAC
addresses use a flexible hierarchical structure.
50. On which switch interface would an administrator configure an IP
address so that the switch can be managed remotely?
FastEthernet0/1
VLAN
1
vty
0
console
0
51. Which two functions are primary functions of a
router? (Choose two.)
packet
forwarding
flow
control
path
selection
microsegmentation
domain
name resolution
52. A network administrator wants to have the same subnet mask for
three subnetworks at a small site. The site has the following networks and
numbers of devices:
Subnetwork A: IP phones – 10 addresses
Subnetwork B: PCs – 8 addresses
Subnetwork C: Printers – 2 addresses
What single subnet mask would be appropriate to use for the three subnetworks?
Subnetwork B: PCs – 8 addresses
Subnetwork C: Printers – 2 addresses
What single subnet mask would be appropriate to use for the three subnetworks?
255.255.255.252
255.255.255.240
255.255.255.0
255.255.255.248
53. What method is used to manage contention-based access on a
wireless network?
token
passing
CSMA/CA
CSMA/CD
priority
ordering
54. Which statement accurately describes a TCP/IP encapsulation
process when a PC is sending data to the network?
Packets
are sent from the network access layer to the transport layer.
Segments
are sent from the transport layer to the internet layer.
Frames
are sent from the network access layer to the internet layer.
Data
is sent from the internet layer to the network access layer.










0 komentar: